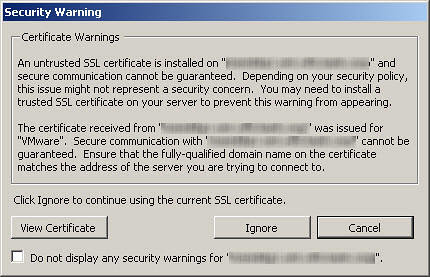
Are you tired of seeing the Security Warning splash screen when launching the Virtual Infrastructure Client to connect to VirtualCenter? Do you feel a sense of guilt clicking the Ignore button or checking the “Do not display any security warnings for…” box? Are you flirting with real world dangers or risking termination for fostering a less secure virtual infrastructure? Would you like to correct the situation the right way by integrating SSL certificates and securing VIC/VirtualCenter communication at the same time? Here are the step by step instructions (originally created by VMTN forum member astrolab and refined by myself).
In this exercise, I’ll be using a Microsoft Active Directory integrated enterprise certificate authority (CA) to generate a certificate for the VirtualCenter host which resides in the same AD domain. We’ll begin with the assumption that the enterprise CA has already been built as well as the VirtualCenter Management Server (VCMS). We will also assume that the enterprise CA is listed as a Trusted Root Certification Authority on the client that will be connecting to the VCMS via the VIC. To validate this in Internet Explorer, choose Tools|Internet Options|Content|Certificates|TRCA tab
- Download and install Win32 OpenSSL Light onto the VCMS http://www.slproweb.com/products/win32openssl.html
- Back up the existing RUI.CRT, RUI.KEY, and RUI.PFX files located in C:\Documents and Settings\All Users\Application Data\VMware\VMware VirtualCenter\SSL\
- Generate an RSA private key and a certificate-signing request (the openssl binary comes from the installation of Win32 OpenSSL Light in step 1 above)
- From a command prompt, change to the C:\openssl\bin\ directory and issue the command openssl genrsa 1024 > rui.key
- From a command prompt, change to the C:\openssl\bin\ directory and issue the command openssl req -new -key rui.key > rui.csr
- Provide the appropriate information. Your Name/Common Name is the FQDN of your VCMS (ie. servername.domain.com)
- Request a certificate from the Microsoft enterprise CA
- In an IE browser, browse to http://enterprise_ca_domain_controller/certsrv/
- Click Request a certificate
- Click advanced certificate request
- Click Submit a certificate request by using a base-64-encoded CMC or PKCS #10 file, or submit a renewal request by using a base-64-encoded PKCS #7 file
- Open the rui.csr file with MS wordpad and copy the entire contents (including the BEGIN and END lines) into the “Saved Requst” field of the certificate request in the web browser. Alternatively, you can click the “Browse to insert” link to simply attach the rui.csr file
- Change the Certificate Template to Web Server
- Click the Submit button
- On the next screen, choose “Base 64 encoded” and click the “Download certificate” link
- When prompted, save the certificate to C:\openssl\bin\ with the file name rui.crt
- Create a .pfx (personal individual exchange) file for rui.crt on the VCMS
- From a command prompt, change to the C:\openssl\bin\ directory and issue the command openssl pkcs12 -export -in rui.crt -inkey rui.key -name VCMSFQDN.domain.com -out rui.pfx
- Move rui.cft, rui.key, and rui.pfx from C:\openssl\bin\ to C:\Documents and Settings\All Users\Application Data\VMware\VMware VirtualCenter\SSL\
- Disconnect all ESX hosts from the VCMS (you can safely leave the guest VMs running or whatever state they are in). This step needs to be done because after the VCMS loads the new certificates, it will not be possible to gracefully shut down the VMs from the VIC, though it could still be done through RDP or COS. It’s best to perform this step to avoid future headaches.
- Stop the VMware VirtualCenter Server service
- From a command prompt, change to the C:\Program Files\VMware\Infrastructure\VirtualCenter Server\ directory and issue the following command to re-encrypt the VCMS database password): vpxd -p (when prompted, type the password used for the VCMS database)
- Start the VMware VirtualCenter Server service
- Reconnect all ESX hosts
- The steps are complete, but there is one important note going forward that deals with the inherent behavior of certificates and our certificate request outlined above: Use the Virtual Infrastructure Client to connect to the VirtualCenter Management Server using the FQDN (ie. server.domain.com). You can connect to the short NetBIOS name of the VCMS but at that point your connection won’t be covered by your certificate and you’ll once again receive the Security Warning dialogue box shown at the beginning of this article.
















I used the thread on the communities forum for reference when I performed my certificate change and onec it was completed I started receiving the unable to decrypt password error when trying to deploy from a template. After rounds and rounds with VMware support I was given the command below for creating the pfx file which solved my decrypt problem. Not sure if anyone else had this problem
%openssl pkcs12 -export -in rui.crt -inkey rui.key -name servername -passout pass:testpassword -out.pfx
Hello webmaster, I’ve been looking for a site like yours since last Wednesday. The last place I searched (should be the first) was in Google, using the keywords “MCSE Certification”. Anyway, it was worth the search because I really like this website and your post regarding egration with VirtualCenter – boche.net – VMware Virtualization Evangelist looks very interesting for me. Definitely Stumbled!
Just what I was looking for. I do have one question and cannot find the answer to it. What is the VCMS db password initially? If I have my sql db on another server other than the VCMS, would it be the db password created there?